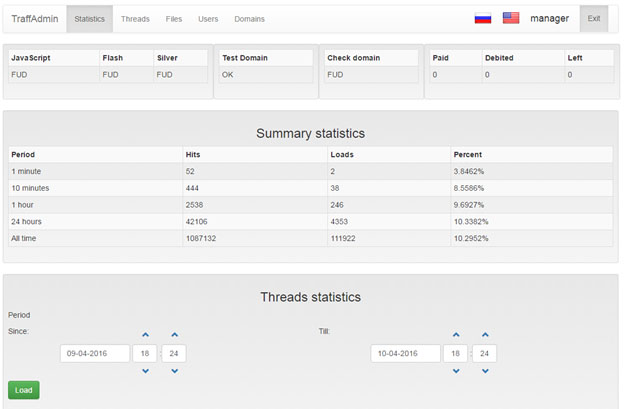
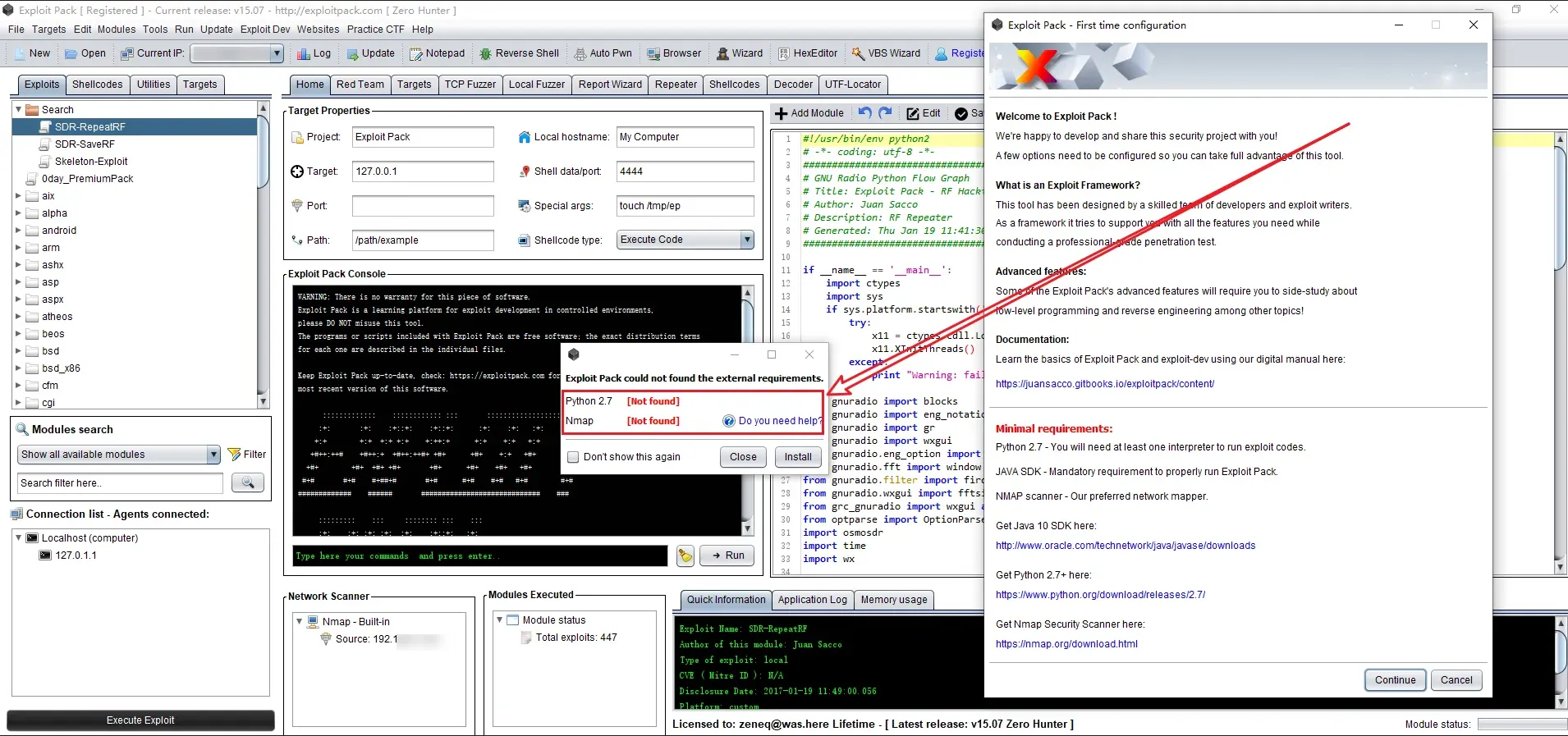
Exploit Pack - Exploit Pack it's a full penetration testing framework that will guide you trough the process of discovering and exploiting new vulnerabilities, but it gets better, it comes built-in with

RIG Exploit Kit Source Code Leak - The End or Just the Beginning of RIG? | Trustwave | SpiderLabs | Trustwave




![Exploit Pack: Point, Click, Root [open-source] : r/netsec Exploit Pack: Point, Click, Root [open-source] : r/netsec](https://external-preview.redd.it/ls33oq8mtTJ3edzn8fxqUjQLU1D0fr_NijXgOJw8p30.jpg?auto=webp&s=915f51344162feaff81020cbbe7db4a9c7a5fa79)

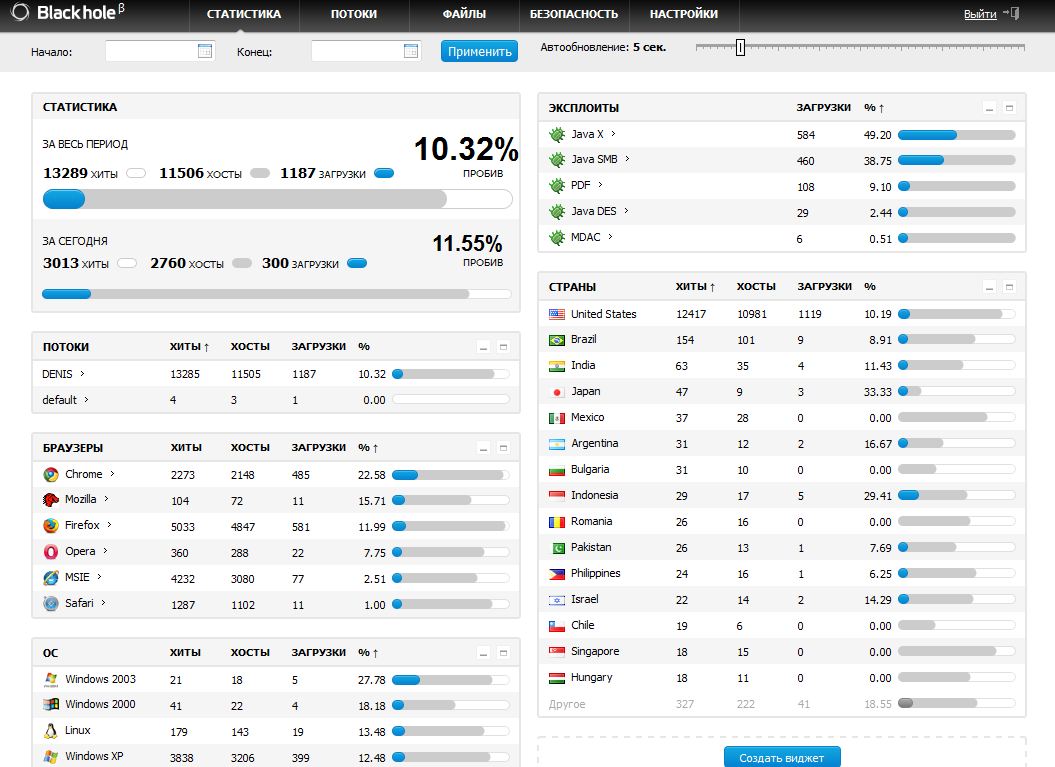
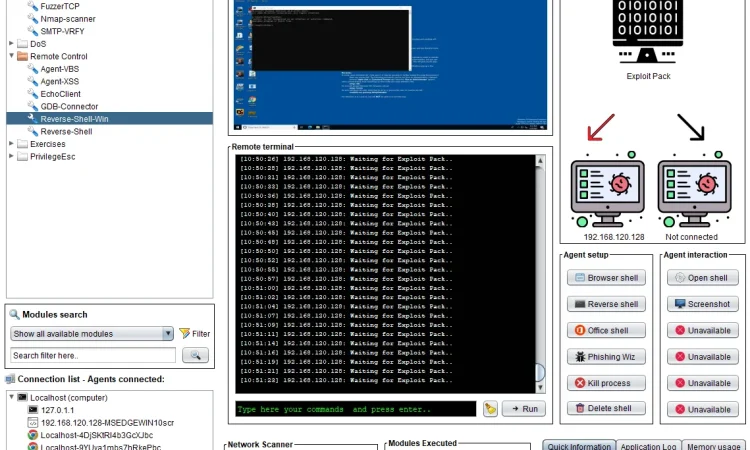
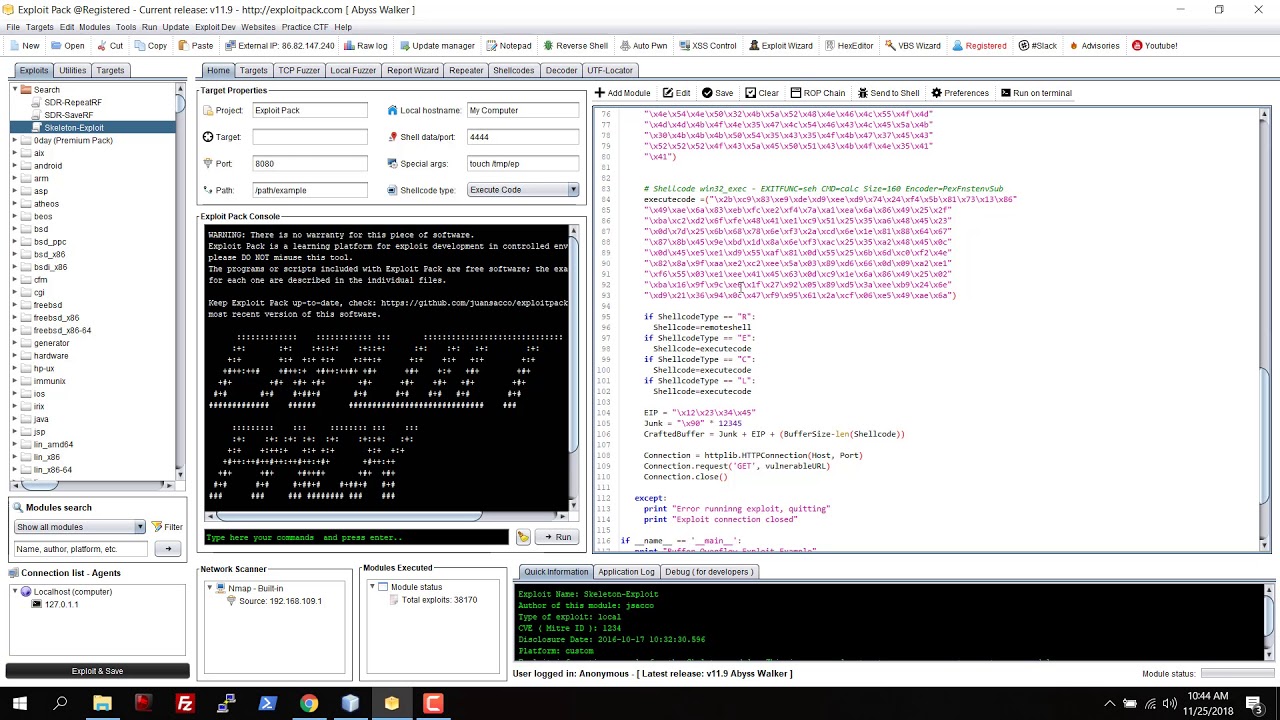







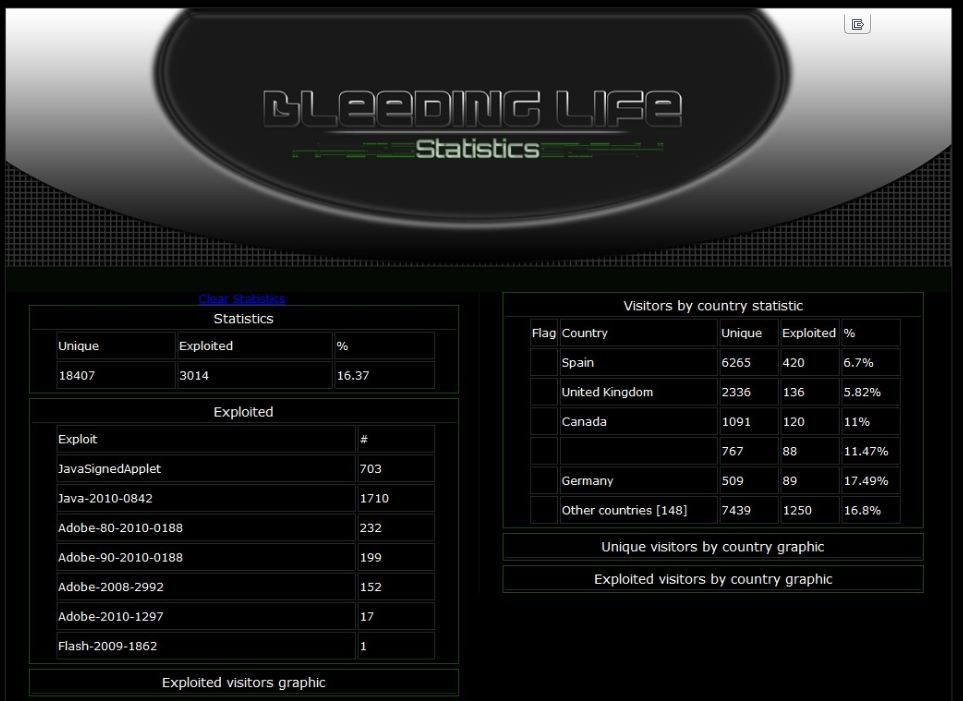
![Exploit Pack] The most advanced and easy to use tool for pentesters Exploit Pack] The most advanced and easy to use tool for pentesters](http://3.bp.blogspot.com/-mv6lYtiOadM/Up_Yr3nulZI/AAAAAAAABSE/R9pYiwI4_xU/s1600/Exploit+Pack.png)